InfraSEC 2025
5 March 2025 Reading time: 2 minutes
Please find the presentation from my talk as a keynote speaker at the InfraSEC conference in Warsaw, Poland on 19/02/2025.
 |
Presentation from my talk at InfraSEC 2025 in Warsaw, Poland about insecurities of industrial systems (PDF). |
A week after the presentation I was positively surprised and honoured knowing that my talk was top-rated by the conference participants!
And THAT news surely made my day!


From free will to wild algorithms: how AI is shaping our lives
6 November 2024 Reading time: 8 minutes
Buckle your seatbelt Dorothy, because privacy is going bye-bye!
It’s not a secret that we all are permanently under observation. We became desensitized and used to it long ago so it is not bothering us too much any more. However, in recent years, the concept of monitoring the lives of humble citizens has evolved much beyond traditional notions of police and state-run agencies. AI has given life to new forms of digital surveillance and methods of collecting information about us. These methods are fast, effective, multidimensional, pervasive and much more intrusive than ever before. These emerging technologies have the power to monitor our every move, almost track our thoughts (so far: indirectly), and control our actions in ways that threaten the very essence of human freedom. Wild imagination? Oh please – read some recent news!
AI-driven surveillance is employed pretty much everywhere these days. It spans from analysis of our behaviour online up to voice and face recognition including monitoring of eye movements. It’s not so difficult really. By using modern high-speed and high-resolution video cameras and machine learning algorithms, computers can now analyse all kinds of behavioural patterns including how you walk, how you talk, and the slightest changes in pupil size and iris to determine everything from our attention span to our political preferences. This data then could be used to infer our personalities, interests, and preferences with alarming accuracy. Technology is progressing so quickly so these days everyone can build a simple surveillance system for fun, e.g. for monitoring your cat. So think about this: if you can build an AI-driven system with Raspberry Pi on one rainy Sunday, think about what governments and large businesses can do with their powerful technology and unlimited resources.
The implications are staggering. In a world where AI-powered algorithms know what we are thinking, feeling, and doing every moment of the day, the concept of privacy becomes an anachronism. Our every move could be tracked and recorded by cameras and sensors that watch us from above, below (and one day probably within). Every transaction, every conversation, and every thought becomes a document. The document can be traced, collected and analysed for clues about our behaviour, preferences, and values. Would I personally ever benefit from it? Doubt. But I am sure, it will be regularly explained to me that it is all happening for my safety, personalised marketing and, surely, for the good of all mankind.
Another prominent example is modern-day elections and voting. I am not referring to the most recent one but to any elections these days. It is totally unclear to me whether the outcome truly reflects voters' genuine desires or is instead influenced by sophisticated state-of-the-art "political engineering". With AI at their disposal, politicians can now create and disseminate tailored messages to millions of people, often without them even realising they're being manipulated. This raises deep concerns that citizens might become unwitting pawns in someone else’s larger agenda, rather than active participants in the democratic process.
Who controls the controller?
The widespread collection of personal data and processing by AI by governments and large corporations raises significant concerns about their accountability. The technology goes forward and these entities can now process and correlate unimaginable amounts of behavioural data on individuals without their knowledge or consent. This starts from browsing history, search queries, location information, biometric data and more. Even innocent metadata which is collected in such vast amounts and processed by AI can tell a lot about an individual. The problem I see is the omnipresent lack of transparency. It creates an opaque situation where individuals have limited or no control (and/or knowledge) over what data was collected, when and by whom. Governments and corporations often justify these practices under the guise of "national security" or "marketing efficiency,". The absence of clear regulations and, first of all, transparent accountability mechanisms means that people have no idea about what is happening with their data, leaving their privacy vulnerable. Let’s not forget that data later can be shared with unknown third parties, who have their own agendas. Data can also be leaked or stolen. Considering all this, probably the only recommendation we can give is: whatever you do online - share as little as possible because everything and anything can be used against you sooner or later. Not an easy task considering that these days we all pretty much never go offline, right?!
But this isn't just a matter of the state watching its citizens. Large businesses and social media platforms aggregate an incredible amount of data on our online activities and create detailed profiles that shape our experiences and interactions. Is there any way we might know what our data is used for? I guess, you know the answer to this question. However, do we truly grasp the implications of this step-by-step erosion of individual freedom? It's leading us towards a dystopian society where every aspect of our lives is constantly in an instant feedback loop with machines, and even the smallest decisions could be dictated by algorithmic manipulation. Probably the meaning of the word “spontaneous” under the circumstances should be redefined. I guess it might be described as “less influenced by the existing behaviour-optimising algorithms”.
By allowing this to happen, we create a society where the boundaries between public and private spaces are disappearing, leaving us all exposed and vulnerable to the whims of our digital masters who wield immense power over human lives. I think a good example of this is Iran's hijab laws. For me, it is a chilling illustration of what happens when AI-powered surveillance is used to enforce rigid conformity and punish dissent. By tracking women's headscarf-wearing habits through facial recognition technology, the authorities have created a system that can identify and penalise those who fail to comply with the regime's strict dress code. This has led to widespread arrests, fines, and even confiscation of property for those deemed to be non-conformists. What if the next decision of the government will be let’s say prohibit women from laughing in public? Could this "law" be enforced with the existing technical measures? Piece of cake.
Do we still have a chance?
In the face of the rapidly advancing proactive and aggressive AI-driven data collection and analysis, it's essential to fully understand the consequences that lie ahead. We're not just talking about a loss of privacy or a threat to civil liberties any more. We are facing a fundamental transformation of human society into a vast global experiment in modification and control of human behaviour. As usual, for the benefit of the chosen few. I can envisage that the AI-powered monitoring systems that are being deployed today have the potential to completely reshape who we are and what we are. Our shopping, working, travelling or dating will never be the same, knowing that not one but many AI Big Brothers are watching and influencing your every step 24/7. Our thoughts and behaviour define us as a species. If our behaviour becomes permanently changed due to the constant influence of technological factors – what does it mean? Are we evolving? Are we going to live in a sort of “symbiotic relationship” with machines? Or maybe degrading?
So, what can we do? First and foremost, we need to be aware of the technologies that surround us and how they're influencing our lives. We must always question the assumptions behind these systems (and their creators) and challenge their right to control our every move. In a world where the reigns of control are gradually given to AI, it's more important than ever to assert our humanity, defend our freedom, and resist the forces of newborn cyber-totalitarianism that might threaten to engulf us all.
We stand at a crossroads in history where the decisions of artificial intelligence systems could shape major historical processes and change the lives of billions. It’s the first time when the algorithms could, literally, make history. The stakes are high, but the battle for human dignity and freedom is not yet lost. The future is never predetermined, but the path ahead is shaped by the choices of all of us. Maybe it is time to learn from history lessons and strive to create AI systems that serve humanity, rather than the other way around.

A tasty cake with security layers
22 October 2024 Reading time: 7 minutes
Imagine a world where no digital activity is fully safe. A world where malicious forces could hijack monetary transactions, private communication and interactions at any time, crippling businesses and lives alike. Sounds like grim science fiction? Take a look: it's our reality today. Cybercrime has become the leading cause of financial loss for companies worldwide, with projected costs reaching a mind-boggling $10.5 trillion annually by 2025.
The threat is very real, and it's not about big corporations anymore; small and medium-sized enterprises (SMEs) are equally vulnerable, accounting for a staggering 43% of cyberattacks. The digital storm rages on, with new threats emerging every day, each more sophisticated than the last. I think it's the right time to start thinking about fortifying your defences!
According to the annual Cost of a Data Breach Report for 2024 from IBM, the global average cost of a data breach has reached an all-time high of $4.45 million, marking a 15% increase over the last three years. Detection and escalation costs also have seen a significant surge of 42%, accounting for the highest portion of the “cost of breach”.
This remarkable growth in breach costs underscores the escalating threat landscape and the need for businesses to fortify their security measures to mitigate risks. The increasing cost is largely attributed to the sophistication and complexity of modern attacks, which demand more time-consuming and resource-intensive investigation and resolution processes.
The secret is in layers
Picture your business as a medieval castle under siege. The walls are breached, and the enemy is at the gates. What do you do? You don't just reinforce one wall, hoping it will hold; you fortify every aspect of your defences - the walls, the towers, the moat, the gatehouse. And that's what we call layered cyber security.
If layered security is in place - it makes it much harder for attackers to breach such a system. Each additional layer increases the complexity and difficulty of breaching the whole system. The concept has been proven effective in various industries, from finance and healthcare to government and manufacturing. For example, banks have notoriously implemented multiple layers of security to protect their customers' money, including network firewalls, intrusion detection systems, encryption, access controls, and, of course, regular software updates. Some studies show that organisations with multi-layered security in place were 70% less likely to experience a data breach compared to those without. Another study by IBM Security revealed that companies using multiple security controls were able to detect breaches 26% faster than those with fewer controls. Why am I not surprised?
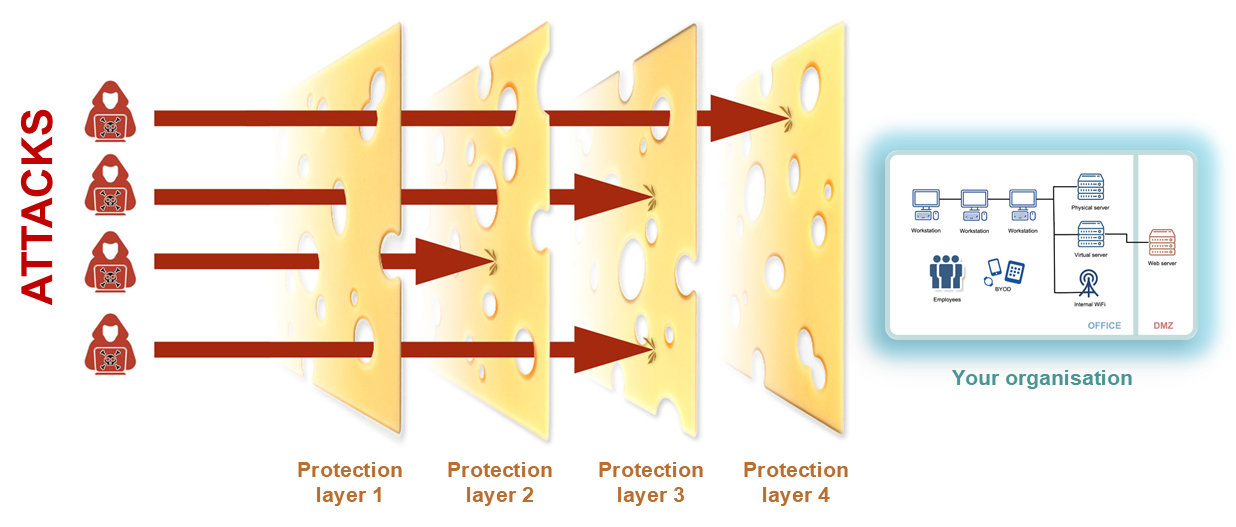
Give me those layers
The core layers of defence are designed to protect against different types of attacks:
- Network security. Your first line of defence is network security, acting as the moat around your castle. Firewalls, intrusion detection systems, and prevention systems control traffic flow, detecting suspicious activity and limiting access. And there is a good reason for having it all. The sheer number of cyber-attacks can be mind-boggling (with estimates ranging wildly depending on the criteria used to define an attack, of course). Some reports claim that as many as 5.5 billion malware infections occur annually, while others put the figure for attempted intrusions at a staggering 6.3 trillion. This means a cyber attack every 3 to 11 seconds!
- Endpoint security. Protecting devices from malware, viruses, and other threats is crucial in today's mobile workforce. Ensure all devices are up-to-date and monitor for threats as they happen. But did you know that 68% of organisations experienced endpoint security incidents in the past year? The threat landscape has never been more daunting.
- Application security. Secure your software with regular testing and updates to patch vulnerabilities and reduce the risk of attacks. The only hope is that your vendor will be delivering those updates and patches promptly.
- Data security. Protect sensitive information in storage by implementing encryption and backing it up regularly to ensure confidentiality and availability. Do you remember the average cost of a data breach from the Cost of a Data Breach Report for 2024 from IBM? Check it again.
- Identity and access management (IAM). Control access to systems and data with strong authentication and role-based access control, safeguarding against insider threats and compromised accounts. IAM is critical in today's world where 70% of organizations face insider threats daily.
Continuous improvement is the only constant
Cybercriminals evolve, and so must your defences. A layered approach is not a set-it-and-forget-it solution; it requires periodic review and adaptation. Start by evaluating your current protection mechanisms regularly, identify gaps, and upgrade whatever is necessary. The future of cyber security surely lies in automated AI-driven tools that process real-time data to predict potential attacks, scale responses, if needed, and put in place advanced monitoring to quickly identify anomalies. But here's a chilling fact: 61% of organisations believe they are not fully prepared to handle a sudden attack. The reality is that no business can afford to wait for the future miracles of AI so thinking about cyber security and investing in security is required right now.
We should not forget that security is everyone's responsibility. Even simple steps like creating strong, unique passwords and being cautious with email attachments can make a significant difference. But even with robust measures in place, internal threats might remain a concern. But in this case, the layered cyber security solutions will help again and address this by implementing stringent access controls and monitoring user activity to catch suspicious behaviour.
A call to action
Cyber security is no longer just an IT issue; it's a business imperative. A multi-layered defence is the only way to stay ahead in today's digital landscape. It requires investment, vigilance, and continuous improvement. So, build your castle with layers of protection - for in this digital storm, the cost of not doing so could be catastrophic.
The stakes are high; the future is uncertain. The choice is yours: invest in cyber security or become another statistic in the ever-growing list of victims of cybercrime. The battle for cyber security is ongoing; ask yourself if you are ready to join the fight.

This is not the WordPress you are looking for
11 October 2024 Reading time: 12 minutes
I know - the topic of web application security is as old as the world. Maybe because I deal with cyber security on a daily basis, it still surprises me why individuals (and businesses) do not really understand the threats waiting for their precious web applications, blogs, corporate portals, web services - pretty much anything accessible online.
Why web applications?
Every Internet-facing web application, portal or any other resource is an immediate, constant and obvious target for hackers for several reasons. I would mention just a few.
First and foremost, web applications are always online. This means that anyone can tinker with them as much as they want. See an illustration below in the section “Website traffic from the kitchen”.
Websites often contain useful and/or sensitive information that hackers might want to steal and use (to be specific: monetise). This could include confidential documents, personal data, or company secrets. Automated scripts can quickly crawl websites to gather all available information or perform tasks without permission from the website owner, leading to unauthorised use of resources or data theft. As a result, hackers might abuse websites “for fun and glory” (read about the recent Internet Archive hack) or to gain financial profit.
Furthermore, Distributed Denial-of-Service (DDoS) attacks can be launched against a website, causing it to become inaccessible and potentially leading to downtime for the site owner's business. Obviously, as a hacker, later you can blackmail the owners and ask for money to stop all this madness.
Did I say that hacked websites could be used to distribute malware which can harm visitors' devices and spread further?
You might be surprised, but Search Engine Optimization (SEO) is another reason why websites are targeted by hackers as they might manipulate search engine results for their own gain.
We should finish this list of reasons by saying that political and social influence is also among other motivations for hacking into websites, such as spreading propaganda or disrupting critical services. Nothing new really.
WordPress, or not WordPress, that is the question
WordPress is surely the most popular Content Management System (CMS) in the world. A quick Google search gives you the astonishing statistics. WordPress powers 43.5% of all websites as their CMS. Around 478 million websites are built on WordPress. It clearly dominates the CMS market with a 62.5% share.
But "with great popularity comes great vulnerability". Despite regular updates and security patches, WordPress remains the most favourite target for hackers. If you are one of the millions of happy WordPress users, be warned - you're on every hacker's hit list "by default"! Here are a few reasons why your WordPress site might be vulnerable
- Outdated plugins and themes. Hackers are very smart and effective: they are very good in quickly finding and exploiting vulnerabilities that haven't been fixed yet and where to look for vulnerabilities but in thousands of WordPress plugins and themes?! With over 65000 plugins and more than 30000 themes available, the potential for vulnerabilities increases with each additional component. Both plugins and themes can introduce many vulnerabilities that put the website at risk. Why? Let me name just a few obvious reasons: the code is poorly written (often not by professional programmers), the software is not tested, and especially: the code is not tested for security.
- Abundance of automated attacks. With millions of WordPress sites, it's a numbers game for hackers using automated tools and scripts for probing and exploitation. And, so far, hackers have won this game.
- Common attack patterns. Hackers often exploit common vulnerabilities in PHP and SQL, which WordPress relies on due to its widespread adoption.
- Poor hosting practices. Insecure hosting environments or shared hosting setups where security measures are lacking can additionally increase the long list of security risks for WordPress sites.
- Poor password security. Weak or default passwords (still!) make it easy for hackers to get in.
- Lack of technical/security expertise. Not all users know how to secure their websites properly. A lack of basic cyber security knowledge leads to childish mistakes.
Most recent WordPress vulnerabilities
I am not sure if you know, but a high-severity vulnerability has been identified in the LiteSpeed Cache plugin for WordPress that could allow malicious actors to execute arbitrary JavaScript code and potentially take control of websites. The stored Cross-Site Scripting (XSS) flaw, tracked as CVE-2024-47374, affects all versions up to 6.5.0.2 and was addressed in version 6.5.1 on September 25, 2024. WordPress users are advised to update the plugin immediately to protect their sites from potential attacks. In short: the vulnerability allows unauthenticated users to inject malicious scripts into websites that have "CSS Combine" and "Generate UCSS" settings enabled. This could result in data theft, privilege escalation, or even a complete takeover of the website if exploited successfully.
This is not an isolated incident, as several other plugins, including TI WooCommerce Wishlist and Jupiter X Core, have also been found with critical security flaws (it should be noted that it was fixed in version 4.7.8). As you can guess, considering all written above, WordPress users are encouraged to stay up-to-date with plugins updates to ensure their sites remain secure (and live happily ever after).
Website traffic "from the kitchen"
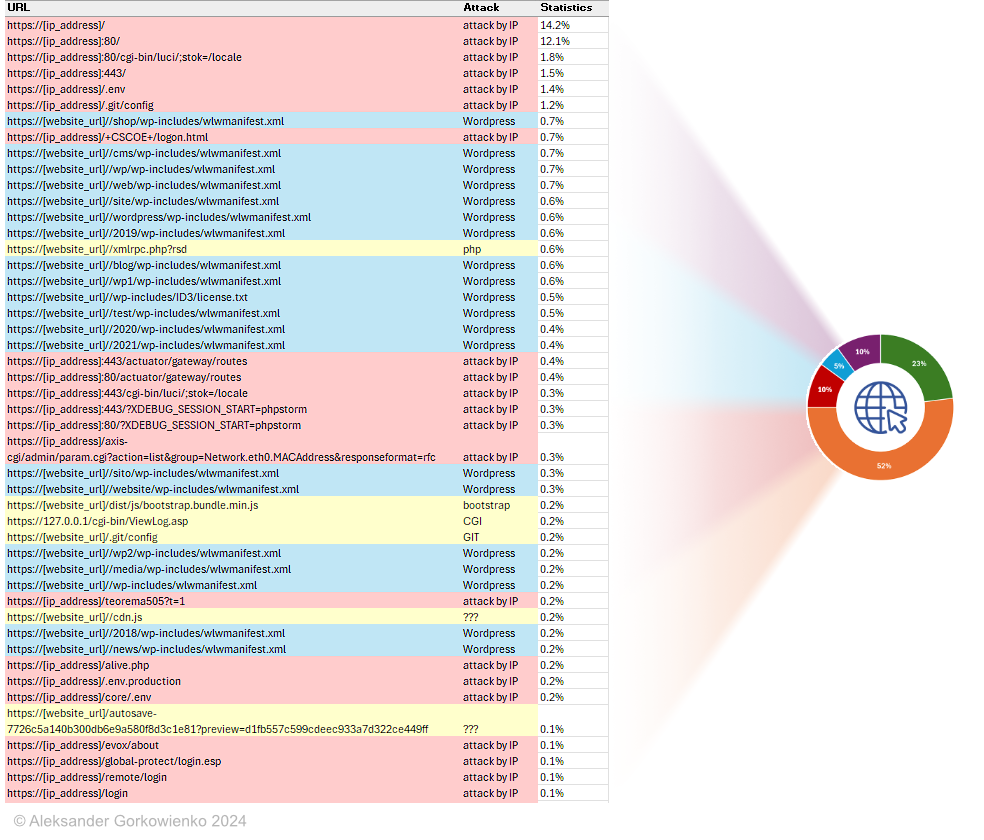
I want to share with you some interesting (and worrying) statistics, based on the incoming requests from the Internet to my own website. I should say right away: my website is not based on WordPress but attackers obviously do not know it. By checking the traffic, I can very quickly see what hackers are after. And this is what I have learnt:
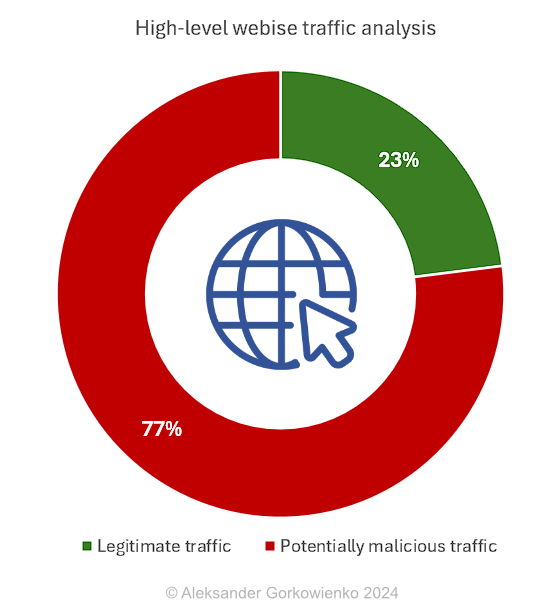
Only 23% of all traffic is related to the website content. All the rest is a massive collection of (predominantly automated) attempts to probe for vulnerabilities of all kinds. So, in short: on a daily basis, 77% of the Internet traffic to my website is malicious. Note: I am talking only about the web traffic, not any usual network scans and probing for open ports - those swipe my server several times a day. Nothing new.
When we take this 77% under a microscope we can see more interesting things.
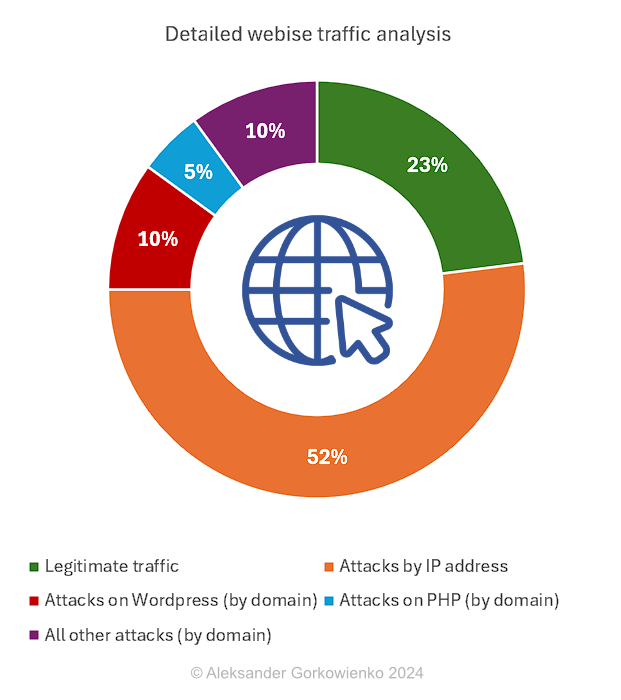
52% of all traffic comes straight to my public IP address, instead of domain. In my opinion, any request by IP should be treated as potentially malicious. Anyone calling your website by IP address surely is not your friend, therefore I would strongly suggest blocking all such requests immediately. Amongst these requests, you can find attempts to find online (well: on my web server) insecure routers, webcams, databases, IoT devices, configuration files (e.g., XML or JSON) specific to various platforms, multiple known attacks to web applications (e.g., SQL injection) and related infrastructure (e.g. buffer overflow). You can learn a lot about what attackers are after simply by checking logs!
Attempts to discover any WordPress-related vulnerabilities take about 10% of all traffic. It’s checking for (non-existing) plugins, config files, versions, etc. About 5% of the traffic is about finding and exploiting PHP-related vulnerabilities and the remaining 10% is a collection of very weird hacking attempts. You can see some of the web queries below.
More requests from my collection. Anyone can tell me what the attacker wants to do in this case (check the requests below)?

The bottom line of this story is that your website or any other Internet-facing resources constantly 24/7 are under attack. If there is any security vulnerability there - it will be discovered sooner or later.
Is there a remedy?
As someone said a long time ago: the most secure web application is the one that is switched off. I will refrain from such dramatic recommendations but, instead, give you a few hints regarding what can be done, especially with WordPress-based websites.
- Use a web application firewall (WAF). A WAF can monitor traffic to detect and block malicious requests, protecting your website from common attacks.
- Block any request to your web application by IP address. You should only allow requests coming by the website domain name. It will cut ¾ of unnecessary web requests.
- Maintain regular updates. Keep WordPress, plugins, and themes up-to-date. This ensures that any security patches or bug fixes are applied promptly, reducing vulnerabilities.
- Keep PHP up-to-date. Regularly update PHP versions on your server as new releases often include security patches.
- Choose secure WordPress themes and plugins. Select themes and plugins only from reputable sources. Avoid those with poor ratings or known issues. Always read reviews before installing new extensions.
- Use strong passwords. Implement strong passwords for your website's admin account and use a secure password manager if necessary. Two-factor authentication (2FA) can further enhance security.
- Make regular backups. Perform regular backups of your WordPress database and files. This ensures you can easily restore your site in case of a hack or data loss.
- Secure file permissions. Ensure that file permissions are set correctly for all files on your server. Use 644 for files and 755 for directories to prevent unauthorised access.
Last but not least:
- Monitor website activity. Regularly check your website's activity logs for any suspicious behaviour or potential vulnerabilities.
- Educate users. Inform users about security best practices, such as avoiding clicking on suspicious links and using strong passwords.
- And, of course, conduct regular penetration tests. Penetration tests are crucial for maintaining web application security by simulating real-world attacks and identifying vulnerabilities that hackers could exploit. They help uncover weaknesses before they're used by hackers, providing valuable insights into the effectiveness of your cyber defences. Penetration testing also helps prioritise security investments and improvements and raises awareness about ongoing security efforts within an organisation.
Once more time, we see that the Internet is not the safest place on Earth. By paying attention to cyber security and implementing these measures, you can surely improve your website's resistance to existing and future hacking attempts. Stay safe!

"Pass the word, Honey" or how the NIST’s new guidelines are changing The Game of Passwords
29 September 2024 Reading time: 4 minutes
Finally, there’s a glimmer of hope at the end of the tunnel for all those tired of remembering insanely complex and frequently changing passwords. Not so long ago (to be specific: on Wednesday, 28 Aug 2024 20:39:12) the National Institute of Standards and Technology (NIST) released its second public draft of SP 800-63-4, providing updated guidance on digital identity verification.
Anyone scrolling through the document would immediately find it long, moderately boring and filled with lots of technical jargon. As you can guess, it certainly would require an extra effort to continue reading and not to give up. To your surprise, NIST’s latest version adds many interesting changes and common sense to password security, challenging many widely used but outdated policies.
Goodbye, password reset madness
One of the interesting changes in the new guidelines is the recommendation to drop the requirement for frequent password changes. Instead of forcing users to change their passwords every month (a practice that originated decades ago when password security was really poor), organisations should focus on monitoring for signs of compromise or credential abuse. This means goodbye to those frustrating mandatory password reset processes that have become a regular nightmare occurrence in our lives. And the best part? It’s based on common sense – forcing users to change their passwords frequently can actually reduce security because people tend to choose weaker ones that are easier to remember.
Sayonara to password nonsense
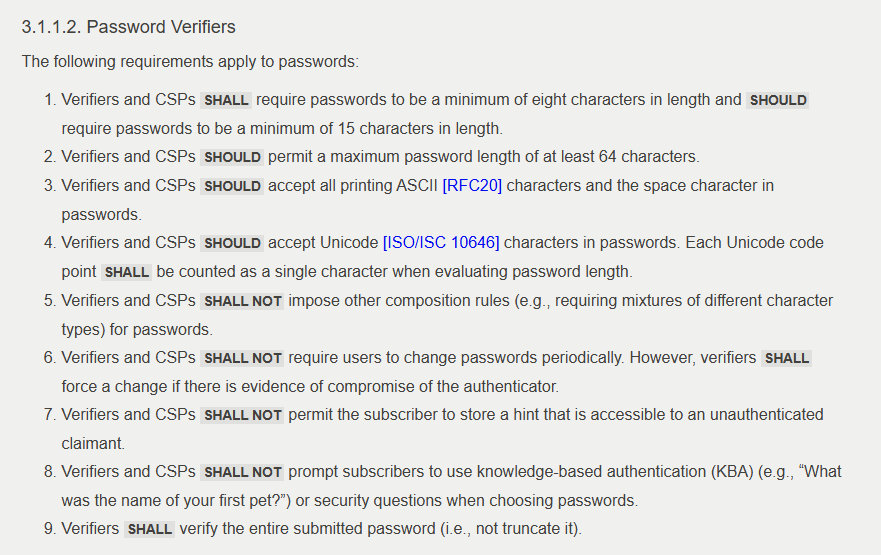
Another exciting change is the acknowledgement by NIST that forcing users to create passwords with specific character composition rules (e.g., “must contain at least one capital letter, one lowercase letter, and a special symbol”) is pointless. This means you can finally ditch those annoying password requirements that make it harder for you to remember your own password. According to the new guidelines, passwords should be at least 8 characters long (with a stronger recommendation of at least 15 characters). It’s simple – just create a strong and random password that works for you.
Ditching security questions
The new guidelines also suggest ditching those easy-to-guess security questions like “What was your mother’s maiden name?” or “What was the name of your first pet?” These were found to be too easy for determined attackers to discover, making them virtually useless for authentication. Instead, multi-factor authentication methods like biometrics or hardware tokens should be used when possible.
Seeing is believing
I know it is not easy to believe in what is said above, but please check the original NIST document or see this extract below:
The benefits of the new guidelines
So what do these changes mean for you? If adopted, these new requirements could significantly enhance online security for individuals and organisations alike. The new NIST guidelines aim to improve digital identity verification, reduce security risks, and eliminate unnecessary burdens on end users with less effort.
While the guidelines are currently only binding for government services and contractors, there’s a chance that other industries will follow. Say goodbye to crazy password policies and hello to simpler, more secure methods of authentication – in the end, we all win.

Dreamscapes less travelled
12 September 2024 Reading time: ~1 minute
The world is a vast and wondrous place, full of hidden treasures and secret destinations waiting to be discovered. But what happens when the journey itself becomes impossible? When the roads end, the seas prove impassable, or the skies refuse to clear? Does that mean our imagination will be silenced, our creative spark extinguished by the "constraints of reality"? of course not! In this digital age, the boundaries of possibility are stretched far and wide, and the limits of what's possible are pushed to new exciting heights. With the power of modern technology at our fingertips, we can now create a breathtaking fusion of art and technology that allows us to capture and share our most fantastic dreams and imagination. From the mist-shrouded mountains of mythical lands to the neon-lit skyscrapers of futuristic cities, these imaginary worlds could be brought to life, pixel by pixel, and shared in a way that's both mesmerising and real. Come and join us on this thrilling journey into the realm of digital dreams, where creativity knows no bounds, and the only limit is your imagination!