"Pass the word, Honey" or how the NIST’s new guidelines are changing The Game of Passwords
29 September 2024 - Reading time: 4 minutes
Finally, there’s a glimmer of hope at the end of the tunnel for all those tired of remembering insanely complex and frequently changing passwords. Not so long ago (to be specific: on Wednesday, 28 Aug 2024 20:39:12) the National Institute of Standards and Technology (NIST) released its second public draft of SP 800-63-4, providing updated guidance on digital identity verification.
Anyone scrolling through the document would immediately find it long, moderately boring and filled with lots of technical jargon. As you can guess, it certainly would require an extra effort to continue reading and not to give up. To your surprise, NIST’s latest version adds many interesting changes and common sense to password security, challenging many widely used but outdated policies.
Goodbye, password reset madness
One of the interesting changes in the new guidelines is the recommendation to drop the requirement for frequent password changes. Instead of forcing users to change their passwords every month (a practice that originated decades ago when password security was really poor), organisations should focus on monitoring for signs of compromise or credential abuse. This means goodbye to those frustrating mandatory password reset processes that have become a regular nightmare occurrence in our lives. And the best part? It’s based on common sense – forcing users to change their passwords frequently can actually reduce security because people tend to choose weaker ones that are easier to remember.
Sayonara to password nonsense
Another exciting change is the acknowledgement by NIST that forcing users to create passwords with specific character composition rules (e.g., “must contain at least one capital letter, one lowercase letter, and a special symbol”) is pointless. This means you can finally ditch those annoying password requirements that make it harder for you to remember your own password. According to the new guidelines, passwords should be at least 8 characters long (with a stronger recommendation of at least 15 characters). It’s simple – just create a strong and random password that works for you.
Ditching security questions
The new guidelines also suggest ditching those easy-to-guess security questions like “What was your mother’s maiden name?” or “What was the name of your first pet?” These were found to be too easy for determined attackers to discover, making them virtually useless for authentication. Instead, multi-factor authentication methods like biometrics or hardware tokens should be used when possible.
Seeing is believing
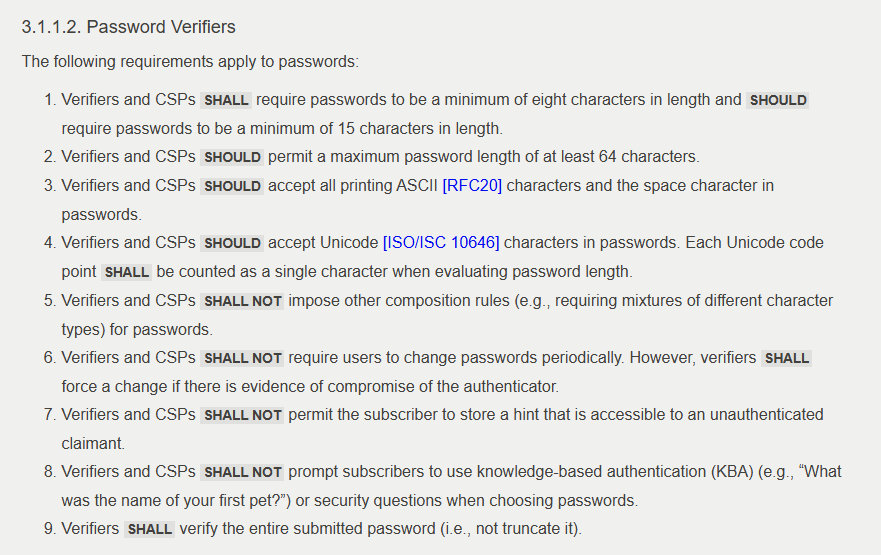
I know it is not easy to believe in what is said above, but please check the original NIST document or see this extract below:
The benefits of the new guidelines
So what do these changes mean for you? If adopted, these new requirements could significantly enhance online security for individuals and organisations alike. The new NIST guidelines aim to improve digital identity verification, reduce security risks, and eliminate unnecessary burdens on end users with less effort.
While the guidelines are currently only binding for government services and contractors, there’s a chance that other industries will follow. Say goodbye to crazy password policies and hello to simpler, more secure methods of authentication – in the end, we all win.