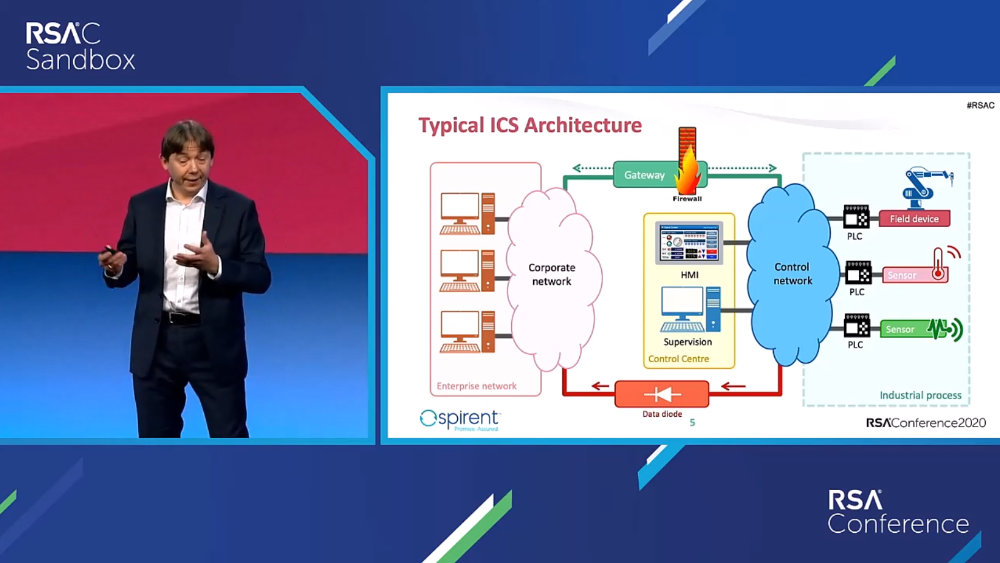
 |
Video from my talk at RSA Conference 2020 in San Francisco about insecurities of industrial systems (ICS/SCADA). This is a real case study demonstrating a creative (and successful) approach to the security assessment of industrial systems. |
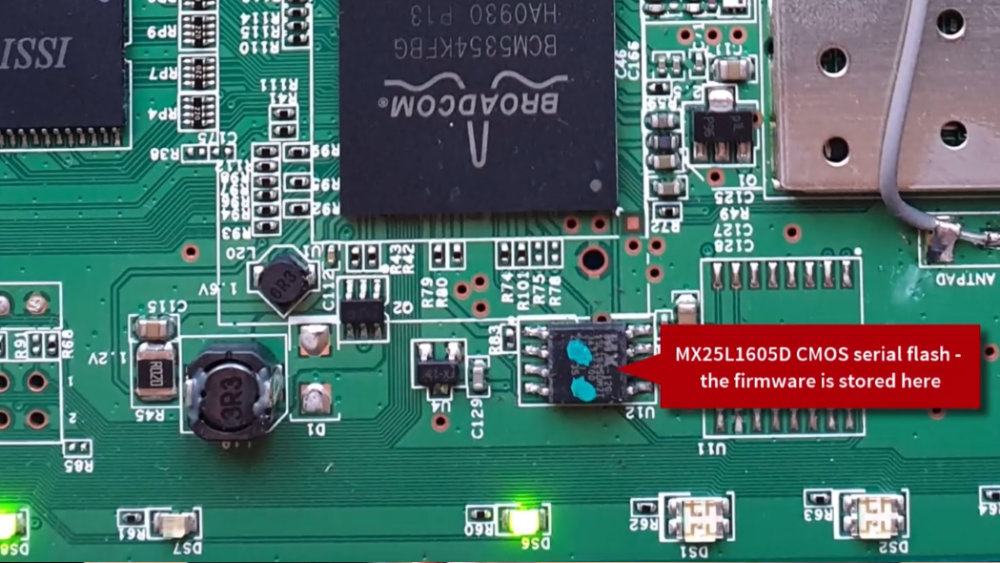 |
An overview of vulnerabilities in hardware devices (in this case: it's a home router) and an illustration of the hacker's/pentester's approach to security analysis and exploitation of embedded/IoT devices. |
 |
This video is about automotive vulnerabilities and illustrates the attack on the car key system by intercepting and decoding wireless signals. |
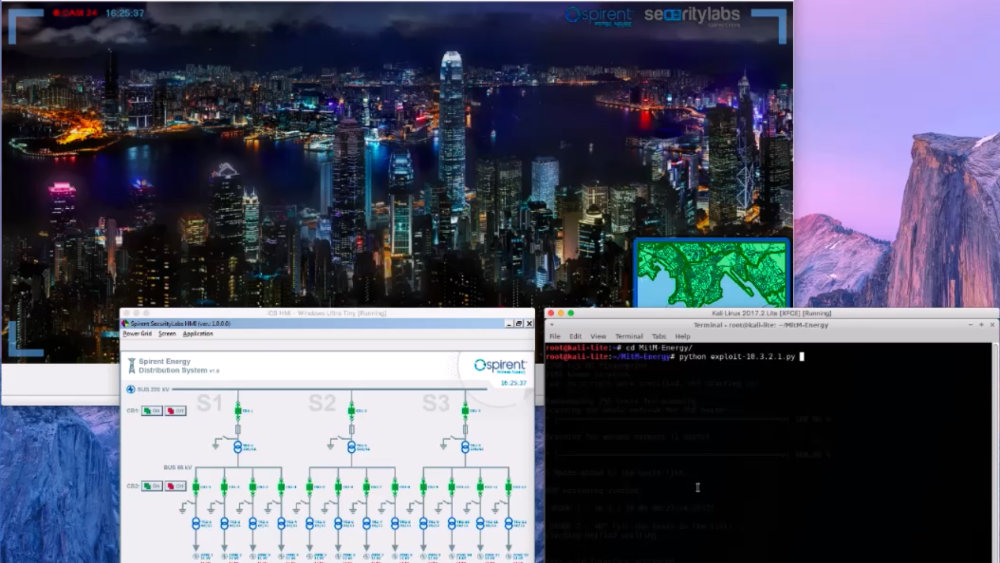 |
Video about vulnerabilities in industrial systems and a demonstration of hackers exploiting electricity distribution systems (e.g., National Grid) (simulated attack). Note that the demo you can see in this video I implemented in software (100% virtualised) and also in hardware. The hardware demonstrator was publicly available at several conferences, such as RSAC and BlackHat Europe. |
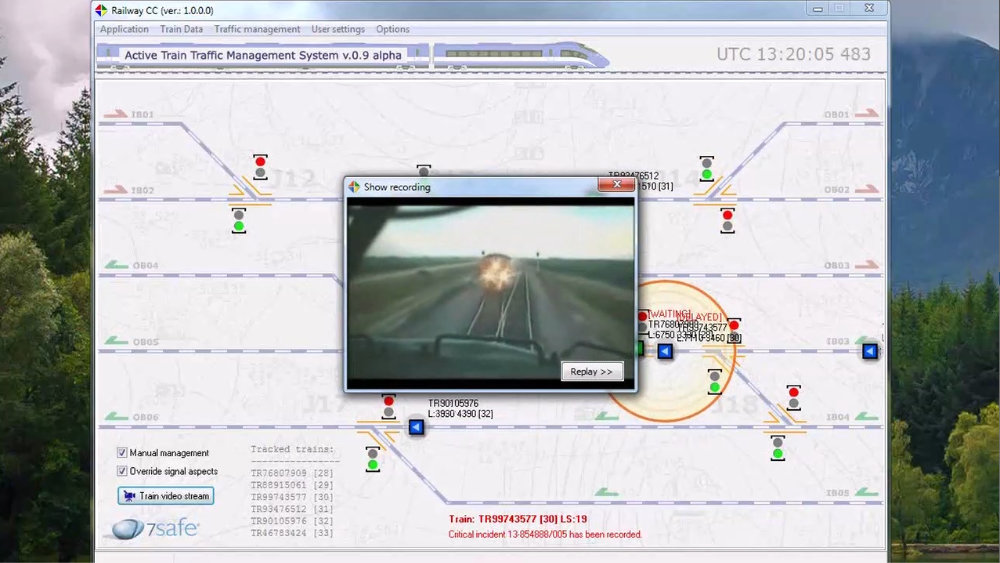 |
This is a video recording of my talk for NetworkRail when I was working for PA Consulting Group. The presentation was about possible vulnerabilities in a train traffic management system (ICS and SCADA) and a demonstration of exploitation by hackers (simulated attack). The attack features SQL injection, weak credentials, client-side HMI GUI manipulation and more. The "train management system" featured in this video was initially designed by me as one of the challenges for the Certified Security Testing Professional (CAST) training course. |
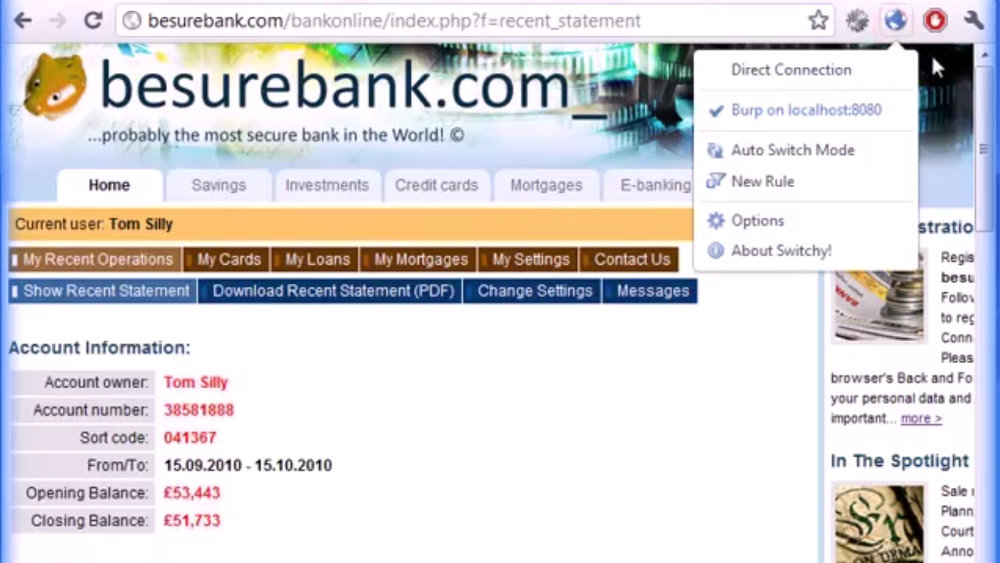 |
Video explaining what Cross Site Scripting (XSS) vulnerability is and how it can be exploited. The video was made when I was working for 7Safe. |
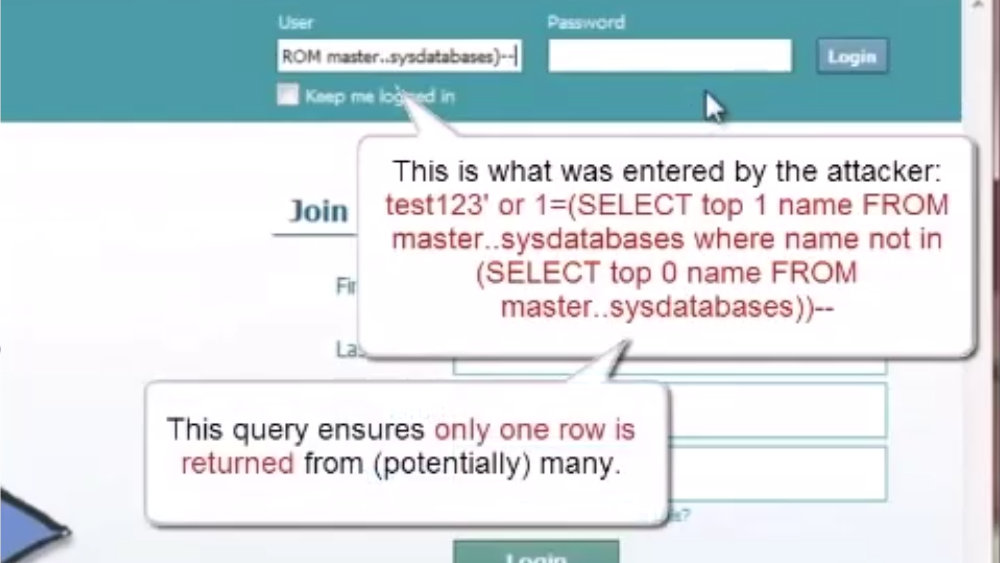 |
Video explaining what SQL injection vulnerability is and how it can be practically exploited. The video was made when I was working for 7Safe. In this video, the viewer can learn about different types of SQL injections (error-based and blind) with step-by-step examples of what are the internal mechanisms of this vulnerability and how it can be exploited. |
 |
An introductory video to the business negotiation course I made for my colleague at the University of Cambridge. The course is about teaching advanced negotiations and the background is a relationship between five fictional countries "Turopian Union". Preparing this video required a lot of graphic design and heavy use of Camtasia. |

