
This is not the WordPress you are looking for
11 October 2024 - Reading time: 12 minutes
I know - the topic of web application security is as old as the world. Maybe because I deal with cyber security on a daily basis, it still surprises me why individuals (and businesses) do not really understand the threats waiting for their precious web applications, blogs, corporate portals, web services - pretty much anything accessible online.
Why web applications?
Every Internet-facing web application, portal or any other resource is an immediate, constant and obvious target for hackers for several reasons. I would mention just a few.
First and foremost, web applications are always online. This means that anyone can tinker with them as much as they want. See an illustration below in the section “Website traffic from the kitchen”.
Websites often contain useful and/or sensitive information that hackers might want to steal and use (to be specific: monetise). This could include confidential documents, personal data, or company secrets. Automated scripts can quickly crawl websites to gather all available information or perform tasks without permission from the website owner, leading to unauthorised use of resources or data theft. As a result, hackers might abuse websites “for fun and glory” (read about the recent Internet Archive hack) or to gain financial profit.
Furthermore, Distributed Denial-of-Service (DDoS) attacks can be launched against a website, causing it to become inaccessible and potentially leading to downtime for the site owner's business. Obviously, as a hacker, later you can blackmail the owners and ask for money to stop all this madness.
Did I say that hacked websites could be used to distribute malware which can harm visitors' devices and spread further?
You might be surprised, but Search Engine Optimization (SEO) is another reason why websites are targeted by hackers as they might manipulate search engine results for their own gain.
We should finish this list of reasons by saying that political and social influence is also among other motivations for hacking into websites, such as spreading propaganda or disrupting critical services. Nothing new really.
WordPress, or not WordPress, that is the question
WordPress is surely the most popular Content Management System (CMS) in the world. A quick Google search gives you the astonishing statistics. WordPress powers 43.5% of all websites as their CMS. Around 478 million websites are built on WordPress. It clearly dominates the CMS market with a 62.5% share.
But "with great popularity comes great vulnerability". Despite regular updates and security patches, WordPress remains the most favourite target for hackers. If you are one of the millions of happy WordPress users, be warned - you're on every hacker's hit list "by default"! Here are a few reasons why your WordPress site might be vulnerable
- Outdated plugins and themes. Hackers are very smart and effective: they are very good in quickly finding and exploiting vulnerabilities that haven't been fixed yet and where to look for vulnerabilities but in thousands of WordPress plugins and themes?! With over 65000 plugins and more than 30000 themes available, the potential for vulnerabilities increases with each additional component. Both plugins and themes can introduce many vulnerabilities that put the website at risk. Why? Let me name just a few obvious reasons: the code is poorly written (often not by professional programmers), the software is not tested, and especially: the code is not tested for security.
- Abundance of automated attacks. With millions of WordPress sites, it's a numbers game for hackers using automated tools and scripts for probing and exploitation. And, so far, hackers have won this game.
- Common attack patterns. Hackers often exploit common vulnerabilities in PHP and SQL, which WordPress relies on due to its widespread adoption.
- Poor hosting practices. Insecure hosting environments or shared hosting setups where security measures are lacking can additionally increase the long list of security risks for WordPress sites.
- Poor password security. Weak or default passwords (still!) make it easy for hackers to get in.
- Lack of technical/security expertise. Not all users know how to secure their websites properly. A lack of basic cyber security knowledge leads to childish mistakes.
Most recent WordPress vulnerabilities
I am not sure if you know, but a high-severity vulnerability has been identified in the LiteSpeed Cache plugin for WordPress that could allow malicious actors to execute arbitrary JavaScript code and potentially take control of websites. The stored Cross-Site Scripting (XSS) flaw, tracked as CVE-2024-47374, affects all versions up to 6.5.0.2 and was addressed in version 6.5.1 on September 25, 2024. WordPress users are advised to update the plugin immediately to protect their sites from potential attacks. In short: the vulnerability allows unauthenticated users to inject malicious scripts into websites that have "CSS Combine" and "Generate UCSS" settings enabled. This could result in data theft, privilege escalation, or even a complete takeover of the website if exploited successfully.
This is not an isolated incident, as several other plugins, including TI WooCommerce Wishlist and Jupiter X Core, have also been found with critical security flaws (it should be noted that it was fixed in version 4.7.8). As you can guess, considering all written above, WordPress users are encouraged to stay up-to-date with plugins updates to ensure their sites remain secure (and live happily ever after).
Website traffic "from the kitchen"
I want to share with you some interesting (and worrying) statistics, based on the incoming requests from the Internet to my own website. I should say right away: my website is not based on WordPress but attackers obviously do not know it. By checking the traffic, I can very quickly see what hackers are after. And this is what I have learnt:
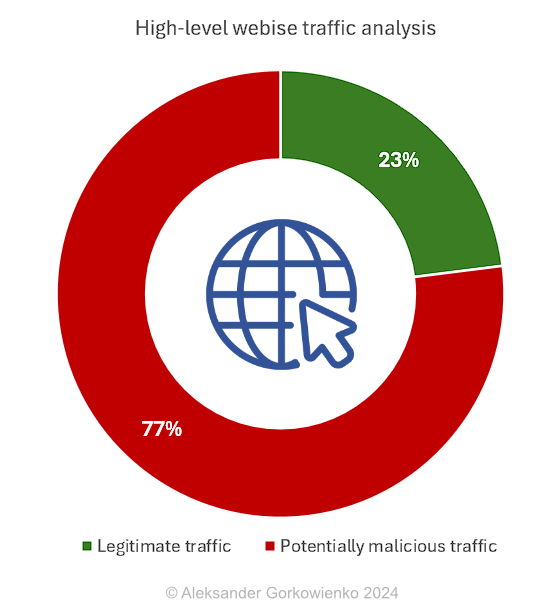
Only 23% of all traffic is related to the website content. All the rest is a massive collection of (predominantly automated) attempts to probe for vulnerabilities of all kinds. So, in short: on a daily basis, 77% of the Internet traffic to my website is malicious. Note: I am talking only about the web traffic, not any usual network scans and probing for open ports - those swipe my server several times a day. Nothing new.
When we take this 77% under a microscope we can see more interesting things.
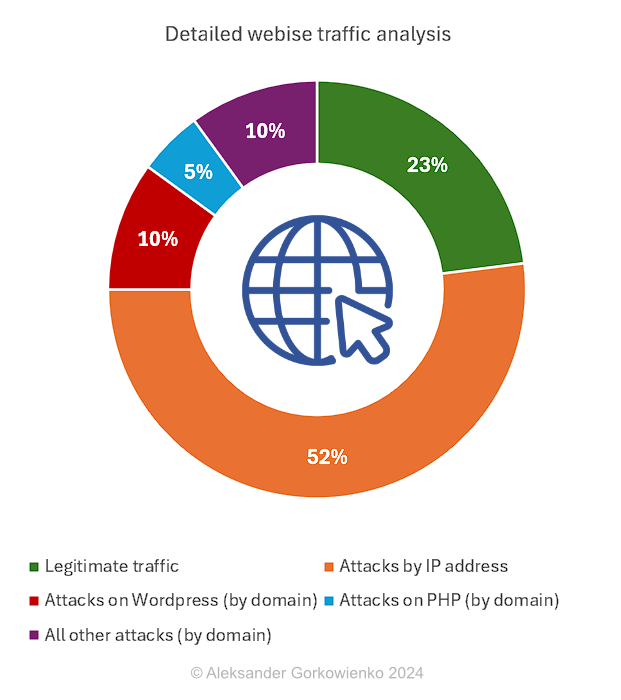
52% of all traffic comes straight to my public IP address, instead of domain. In my opinion, any request by IP should be treated as potentially malicious. Anyone calling your website by IP address surely is not your friend, therefore I would strongly suggest blocking all such requests immediately. Amongst these requests, you can find attempts to find online (well: on my web server) insecure routers, webcams, databases, IoT devices, configuration files (e.g., XML or JSON) specific to various platforms, multiple known attacks to web applications (e.g., SQL injection) and related infrastructure (e.g. buffer overflow). You can learn a lot about what attackers are after simply by checking logs!
Attempts to discover any WordPress-related vulnerabilities take about 10% of all traffic. It’s checking for (non-existing) plugins, config files, versions, etc. About 5% of the traffic is about finding and exploiting PHP-related vulnerabilities and the remaining 10% is a collection of very weird hacking attempts. You can see some of the web queries below.
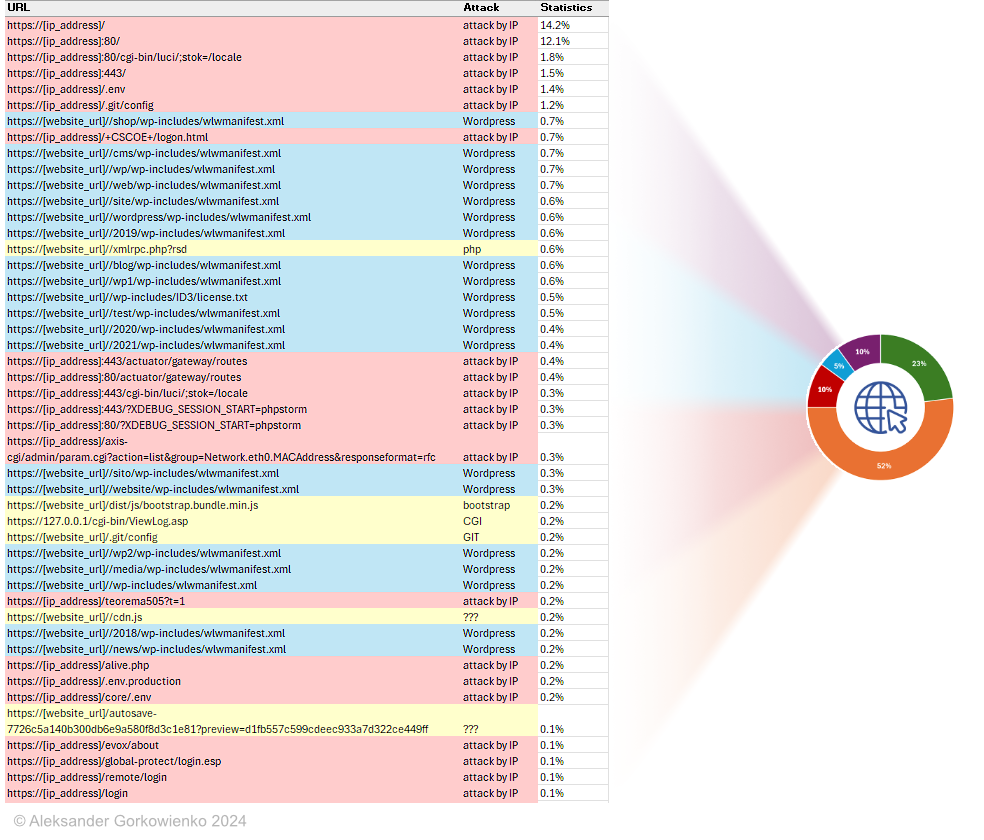
More requests from my collection. Anyone can tell me what the attacker wants to do in this case (check the requests below)?

The bottom line of this story is that your website or any other Internet-facing resources constantly 24/7 are under attack. If there is any security vulnerability there - it will be discovered sooner or later.
Is there a remedy?
As someone said a long time ago: the most secure web application is the one that is switched off. I will refrain from such dramatic recommendations but, instead, give you a few hints regarding what can be done, especially with WordPress-based websites.
- Use a web application firewall (WAF). A WAF can monitor traffic to detect and block malicious requests, protecting your website from common attacks.
- Block any request to your web application by IP address. You should only allow requests coming by the website domain name. It will cut ¾ of unnecessary web requests.
- Maintain regular updates. Keep WordPress, plugins, and themes up-to-date. This ensures that any security patches or bug fixes are applied promptly, reducing vulnerabilities.
- Keep PHP up-to-date. Regularly update PHP versions on your server as new releases often include security patches.
- Choose secure WordPress themes and plugins. Select themes and plugins only from reputable sources. Avoid those with poor ratings or known issues. Always read reviews before installing new extensions.
- Use strong passwords. Implement strong passwords for your website's admin account and use a secure password manager if necessary. Two-factor authentication (2FA) can further enhance security.
- Make regular backups. Perform regular backups of your WordPress database and files. This ensures you can easily restore your site in case of a hack or data loss.
- Secure file permissions. Ensure that file permissions are set correctly for all files on your server. Use 644 for files and 755 for directories to prevent unauthorised access.
Last but not least:
- Monitor website activity. Regularly check your website's activity logs for any suspicious behaviour or potential vulnerabilities.
- Educate users. Inform users about security best practices, such as avoiding clicking on suspicious links and using strong passwords.
- And, of course, conduct regular penetration tests. Penetration tests are crucial for maintaining web application security by simulating real-world attacks and identifying vulnerabilities that hackers could exploit. They help uncover weaknesses before they're used by hackers, providing valuable insights into the effectiveness of your cyber defences. Penetration testing also helps prioritise security investments and improvements and raises awareness about ongoing security efforts within an organisation.
Once more time, we see that the Internet is not the safest place on Earth. By paying attention to cyber security and implementing these measures, you can surely improve your website's resistance to existing and future hacking attempts. Stay safe!