
Deciphering 5G security (Part 3). The one about the security of the 5G telecommunication supply chain.
22 November 2023 Reading time: 10 minutes
My dear readers, today is the day when we spend some leisure time exploring a truly exciting topic. The topic becomes even more thrilling when we apply it to telecommunication and 5G. Of course, I am talking about the security of the supply chain. So shall we start?
Everything you always wanted to know about supply chain [in]security but were afraid to ask
Many critical IT systems handling essential services like emergency services, healthcare, energy production and distribution and also telecommunication - all present lucrative targets to hackers. But let's not forget: critical national infrastructure (CNI), by definition, is, well, critical, so typically it is sufficiently protected. Cybercriminals, of course, do not want to waste their valuable time on exploitation where the probability of success is questionable. They, however, are very happy to target CNI indirectly, and it can be done through the compromised supply chains. Hackers have tons of good reasons for that:
Leverage of trust: victims are likely to implicitly trust routine updates/patches from their software vendors and install them without scrutiny. This human factor plays very well into the hands of attackers.
Amplified access: by compromising a single supplier, attackers can potentially gain indirect access to all of that supplier's customers simultaneously. This substantially increases the impact and number of potential victims.
Persistence: once embedded in a supplier's update mechanisms, the attacker's malicious code can persist hidden across numerous networks for a long time before detection.
Attacks self-propagation: compromised updates can then infect new victims automatically as they are installed, requiring little effort from the attacker to spread widely.
I can call it "Diversion of blame": the convoluted path makes incidents much harder to trace back to the original intruder and diverts suspicion to other entities.
High level of disruption: affected critical infrastructure components, can induce serious economic and operational damage across entire sectors.
So, in short, supply chain attacks provide enough advantages making them very tempting from an attacker's standpoint. Maybe that's why we have plenty of such attacks already. And, surely, there will be even more in the near future.
One of the prominent recent examples that is still fresh in everyone's memory is, of course, the SolarWinds breach. It perfectly demonstrated how compromising a supplier can enable broad access to downstream customers by installing tainted software updates. The incident began with malicious actors gaining unauthorised access to SolarWinds' internal systems where they developed their Orion monitoring platform. From this compromised infrastructure, the attackers were able to generate and disseminate "tweaked" software updates containing hidden malicious code. The SolarWinds happy customers were not expecting anything bad and applied these tainted software patches in their environments. As you can guess, unfortunately, they were immediately compromised and subsequently infiltrated, with the hackers using those pivoting positions to move deeper inside organisational networks and systems. By targeting the supplier first, the attackers enabled themselves almost perfect widespread passive access across SolarWinds' vast customer base of users routinely installing the benign-looking yet very much malicious platform updates.
Surely, the story is well-known, but there is one important detail here. The timeline of events shows that the attack did not happen overnight. It took hackers a good few years to prepare, compromise the supplier, retain access, slowly infiltrate and modify the software development lifecycle and finally enjoy the results when the malware was up and running at hundreds of the customers' systems. So now close your eyes and think about what measures your company should have in place to be able to identify and prevent such attacks.
It looks pretty bad already, right? Alfred Hitchcock used to say once: "Any good film should start with an earthquake and be followed by constantly rising tension". So now, shall we turn up the heat even further and think about what could happen if the same attack pattern is applied to the telecommunication systems and, specifically, to the subject matter: our beloved 5G? You will immediately see that there are even more reasons why attacking the 5G telecommunication supply chain is a sweet dream for cyber attackers.
5G supply chain blues
I have touched on 5G security in the previous articles, so here let's just do a quick recap. 5G differs fundamentally from previous cellular architectures in several ways. Rather than being physical and monolithic, 5G leverages a fully virtualised model that is distributed across the network. Through network functions virtualisation, 5G enables the dynamic creation of virtual network functions (VNFs) independently of dedicated hardware. This allows agile deployment and extension of practically any functionality on demand wherever and whenever needed. The network could be also partitioned into isolated "slices" optimised for diverse usage scenarios, allocating dedicated resources without interference (at least "by the book"). Finally, 5G does not rely solely on centralised base stations but utilises distributed user plane functions which swiftly route traffic with low latency. Needless to say, such architecture, featuring hundreds of NFs from countless suppliers, "somehow" assembled by a mobile network operator, creates many exciting opportunities for attackers. But for now, let's focus on the supply chain problems only.
In the telecommunication world, common supply chain-related security targets include third-party suppliers of hardware and software and all the communication and transit paths of software and hardware travelling from suppliers to MNOs. Telco supply chain attacks could bring even more joy to hackers for the following reasons (this is not a complete list):
Default weak security oversight: many suppliers of software or 5G NFs have a "rather-not-perfect" security in their SDLC, to say the least. Therefore, this complex sector presents fantastic opportunities for determined attackers to gain footholds.
Mass disruption potential: telco networks are a part of CNI that support numerous other sectors. Disrupting these networks through a supply chain attack could cause a widespread damaging impact.
Access to sensitive data: by their nature, telco networks carry vast amounts of personal and corporate precious communications data. Implanted malware could steal this private information over time.
Exploit the Internet of Things: more and more devices are Internet-connected and many (especially lonely and remote ones) are relying on telecommunication networks. Compromised updates could spread to IoT devices, which can join botnets, suddenly become evil, etc.
Geopolitical leverage: many nation-state malicious actors could use telecommunication supply chain attacks to gain intelligence or sabotage capabilities against rival governments and/or industries.
Long-term persistence: telecommunication equipment is relied on for decades. Implanting malware guarantees long-lived backdoors in critical systems.
As each network slice and virtualised function can potentially become a target, a failure to properly isolate these elements through segmentation could enable compromises to cascade and potentially cripple the entire system. A successful infiltration of even a single virtual component could paralyse its operations. Further, without adequate countermeasures, an infected segment risks propagating the issue throughout the network, bringing down 5G core functionality.
Is there light at the end of the tunnel?
The rollout of 5G promises many benefits, however, the new architecture of 5G networks also inevitably introduces unique security challenges that need to be addressed throughout the supply chain. Let's discuss some key strategies for preventing and mitigating supply chain risks in 5G (this is also not a complete list).
Thoroughly vet suppliers. With so many interconnected entities involved in the supply chain, the vulnerabilities of the weakest link become everyone's problem. It is advised to conduct regular risk assessments of third parties and audit their security practices. Only work with trusted partners who can demonstrate protections at least equivalent to your own if not better.
Establish a root of trust. One of the important lines of defence is making sure there is a verified root of trust embedded in all mobile network components. This could involve technologies like hardware security modules that can attest to a device's integrity before it connects. Having a trusted identity will make it harder for compromised components to infiltrate the network and stay undetected.
Implement strong authentication. Within 5G's network, each VNF will expose its own attack surface. Strong authentication should be deployed across all layers to strictly control and monitor access. Encryption techniques can also encrypt individual data flows between NFs and hardware to limit the "blast radius" in case of intrusion.
Continuously monitor for anomalies. As 5G networks grow more complex and decentralised, threats will become harder for humans to identify manually. Investing in network and user behaviour analytics solutions that leverage AI/ML can help automatically detect anomalies indicative of attacks or malfunctions. Continuous monitoring and logging are the key to rapid remediation. You can't manage what you can't measure.
Isolate and segment critical functions. Should threats be detected, there should be existing mechanisms which could automatically terminate affected credentials, isolate compromised network slices or NFs, and redistribute traffic automatically. This "zero trust" approach limits lateral movement and prevents single points of failure from cascading impacts. Granular access controls and micro-segmentation help contain incidents.
The bottom line
By taking a holistic, vigilant approach with people, processes and technologies working in tandem, 5G networks can achieve their transformative potential. While mitigating risks to the supply chain no single control is enough - robust security demands continual vigilance across all domains. A layered defence strategy with verifiable device identities, adaptive access controls, real-time analytics and agile containment mechanisms can help mobile network operators navigate the 5G threat landscape. However, diligence must be an ongoing priority for all stakeholders.

Deciphering 5G security (Part 2). The one not about the elephant but O-RANgutan in the room.
16 November 2023 Reading time: 9 minutes
When our countless mobile devices connect to the nearest cell tower, communication occurs over the radio access network (RAN). The RAN facilitates air interface connections to the tower, which then routes signals via fibre or wireless backhaul to the heart (core) of the telecommunication network.
Traditionally, RANs have been proprietary in nature, integrated solely with individual equipment manufacturers' systems (like Ericsson, Nokia, Huawei, etc.). So, in a typical MNO's dream, they pay an insane amount of money to the vendor, then unpack a huge delivery box(s), turn the key and magically everything works. At least in theory. Truth or not, it's all in the past.
Why O-RAN?
In contrast, Open RAN (or: O-RAN) supports interoperability through standardised interfaces that enable network operators to incorporate multi-vendor sub-components like remote radio heads and distributed units. This new architecture aims to achieve three primary objectives.
- It pursues "cloudification" (oh, I really don't like this word for some reason) through disaggregated and software-based network functions that can leverage the beauty of modern cloud-native computing platforms.
- O-RAN supports open internal interfaces between network components, naturally, including standards defined by 3GPP. This objective seeks to define standardised communication protocols that enable interoperability across a diverse set of O-RAN component suppliers.
- O-RAN facilitates increased intelligence and automation. By incorporating advanced capabilities like AI/ML, it is now possible to better automate the management and orchestration of RAN resources.
This shift to disaggregated and interoperable RAN architectures inevitably introduces more flexibility and choice. However, it also seriously complicates network configurations due to the integration of many varied third-party elements, of course, coming from different vendors. As a result, the "default" security risk profile for wireless networking is severely altered under O-RAN deployments, with orchestration and segmentation challenges that previously did not exist within closed, proprietary implementations.
I think no one is surprised that there was someone who desired to put it all in order. And this heavy job was taken by the O-RAN Alliance - a group of mobile operators, vendors and researchers working to define that whole open and intelligent RAN ecosystem. The Alliance develops standards and specifications for open interfaces between network components to facilitate that much-needed multi-vendor interoperability. It also establishes reference architectures and designs for O-RAN elements. I say they are generally doing a really good job and deliver tons of useful documentation. However, we should also admit that this task is complex and all the standards go through an iterative process, sometimes lagging behind the urgent needs of the telecommunication industry. And this leaves some space for (hopefully constructive) critique. In 2021, Germany's Federal Cyber Security Authority conducted a risk assessment of the O-RAN Alliance's standards and architectural framework. Their analysis considered requirements around confidentiality, integrity, accountability, availability and privacy from the perspective of end users, network operators, and national interests. Surprisingly (or not), the results indicated e.g., that some interfaces and components specified in O-RAN could have almost immediately introduced various medium to high-security risks "by design"! Also, well-known zero-trust and "security by design" practices also did not seem to factor strongly enough into the specifications. But, luckily, everything evolves and the existing O-RAN specifications in 2023 are much more robust and truly leading the way.
Unfortunately, it does not mean that there are no more security risks for O-RAN.
In 2022 EU published a report on the security of O-RAN. The report outlined some potential risks, such as, e.g., a much wider attack surface resulting from the disaggregated architecture. With more vendors and interfaces involved, this means that there are increased opportunities for exploitation. Additionally, the O-RAN components could have various misconfiguration issues and those flaws may have greater impacts as well, given the shared infrastructure approach and resource pooling across network functions. Not surprisingy, this time, the report also raised concerns about O-RAN security not being sufficiently prioritised from the beginning. Some researchers are even attributing this to slower O-RAN adoption in Europe, e.g., compared to Japan.
Let's summarize the key O-RAN security risks.
- Dependence on cloud infrastructure introduces multiple new avenues of attack and single points of failure that challenge O-RAN secure management at scale.
- A multi-vendor ecosystem with diverse, interoperable systems complicates coordination, visibility, authentication and change management across the disaggregated architecture.
- Legacy O-RAN components manufacturers are still building core security capabilities as they transition to software-defined models, potentially leaving early-generation (legacy) systems exposed and vulnerable.
- Incorporation of third-party open source code brings many risks like missed/overlooked vulnerabilities or even backdoors waiting quietly in depths of shared libraries outside of operator purview.
- Utilisation of shared spectrum for critical access broadens the potential attack surface and raises risks of availability issues from interference or DoS of the shared resources.
How to ensure O-RAN is secured?
Follow the cybersecurity best practices. The EU has released several documents in recent years highlighting cybersecurity challenges for next-generation telecommunications infrastructure, such as EU Toolbox and various subsequent risk reports (google: 5G ENISA). All of them called attention to issues that will need ongoing mitigation as 5G networks evolve. Security concerns related to Open RAN architectures are actively being evaluated both within standards development forums as well as broader industry discussions. The security risks could be greatly reduced if the best practices are in place, such as security by design, adopting compliance standards, conducting regular risk assessments, configuration management, minimizing attack surface area, proper patch management, monitoring and logging and incident response planning.
Control your supply chain and buy O-RAN components from trusted vendors only. Let's start from this: leading vendors always invest heavily in security R&D and integrate defences proactively into new product designs. "Security-by-design" is not just a nice slogan for them. Trusted vendors also are much less likely to accidentally introduce malware or backdoors in hardware/software components during development and manufacturing. This automatically reduces many supply chain risks. Established vendors typically have dedicated security teams and processes for identifying vulnerabilities and issuing patches/updates - this level of security maturity is lacking in some smaller component makers. Last but not least: trusted vendors also follow international security standards and regulations. Their components are more likely to be compliant with requirements regarding privacy, encryption, authentication etc. out of the box.
Conduct thorough and regular security assessments. This means regular penetration testing aiming to find weaknesses before attackers can at the device level, assembled subsystems and system levels. Penetration testing can greatly help to improve O-RAN security by ticking these boxes:
- Identify hard-to-find vulnerabilities: Penetration tests actively try to exploit systems to uncover O-RAN security weaknesses before attackers do. This allows issues to be remediated. Prevention is always better than cure.
- Validate defences: Thorough testing puts O-RAN implementations through real-world attack simulations to ensure controls and countermeasures are functioning as intended.
- Surface misconfigurations: Pentests often discover vulnerabilities created by improper configurations, outdated software, or unclear access policies.
- Test patches: Repeated testing confirms security updates and new versions close previously identified vulnerabilities as intended.
- Evaluate risk exposure: Test results provide insight into the most severe weaknesses to prioritize remediation of the highest risks first.
- Stress test systems: Pushing systems to their limits through various exploit methods helps validate performance and resiliency under duress.
- Verify segmentation: Tests determine if control measures properly separate domains to contain lateral movement if one is breached.
- Audit suppliers: Pentests of third-party components validate suppliers' claims before integration into an operator's precious network.
Forewarned is forearmed.
While the benefits of O-RAN in terms of flexibility, optimisation, and cost savings are undeniable, it is critical that network operators and other stakeholders carefully consider the cybersecurity challenges that an open and virtualised architecture introduces. As we have discussed, the multi-vendor ecosystem, reliance on cloud infrastructure, use of open-source code, and increased complexity all contribute to a larger potential attack surface. However, by enforcing best practices many of these risks can be successfully mitigated. Those who embrace O-RAN by prioritising security from the start will be best positioned to reap the rewards of innovation while ensuring the resilient defence of their precious critical network infrastructure. As they used to say in Polish: "przezorny zawsze ubezpieczony" or "forewarned is forearmed".

Deciphering 5G security (Part 1). Separating Facts from Fiction.
14 November 2023 Reading time: 4 minutes
As the hype (oh sorry, better call it: general excitement) around 5G continues to grow, the network of the future seems poised to change telecommunications forever and in a good way. However, as with any new technology, 5G also introduces new risks that could undermine its potential if not properly addressed. In the series of articles I want us to find out what those risks are and how to deal with them before it's too late.
5G is indeed thought to be a new market force, bringing wireless connectivity to billions more devices. Its massive machine-type communication capabilities alone have the potential to power new IoT use cases we can barely imagine today. But the scale and hyper-connectivity of 5G networks also mean new avenues for threat actors to exploit.
Some could say: read the specs! The security is "embedded in 5G" from the ground. The new architecture utilises a myriad of security features implemented throughout the whole network. User data and signalling traffic traversing both the control plane overseeing network operations and the user plane carrying subscriber data are encrypted. Encryption is also applied to subscriber identities and interfaces between network components. Additionally, 5G SA mandates Transport Layer Security (TLS) encryption and authentication for communication between different mobile network operators. So is there a problem here? Yes, there is: take a look.
For example, 5G network functions (NFs) are software-based and come from many different vendors. Those NFs will certainly introduce vulnerabilities if patches or security updates are not correctly (and promptly) applied. New authentication mechanisms, mandated by the 3GPP standard, may also require strengthening to prevent unauthorized access, e.g. to core network slices. On the RAN side, open interfaces in OpenRAN architectures could expose control planes if not properly firewalled and segmented. There are also concerns around supply chain integrity as 5G infrastructure is sourced globally. Without robust vetting and oversight of contracting parties, could certain components become vehicles for embedding hidden vulnerabilities or backdoors? Well, supply chain security would surely require a separate long and interesting conversation.
But this is not the end of the story. 5GC introduces even more risks due to its use of open HTTP/2-based APIs, and a large number of dynamically scalable microservices within each NF that talk to each other primarily through public interfaces rather than proprietary protocols. While this architecture features cloud-native technologies and speeds up development and remediation, - at the same time it also provides many more familiar attack vectors for malicious actors. To maintain resilience against both intentional and unintentional threats mobile operators must start thinking now about how to improve security measures across their 5GC systems. There is one more reason for it: new draconian legislation in Europe and in the UK. If things go wrong - the poor telco has to pay a fine of up to 2% of the global yearly revenue (I am referring to NIS 2, as you might rightfully guess). Indeed, this gives some food for thought. The stakes are high as operators have to deal with challenges that substantially exceed any risks faced in earlier cellular generations.
In my humble opinion, the only reasonable approach is to make security testing not optional but mandatory for all 5G network functions, configurations and software deployments. This should include regular penetration testing aiming to find weaknesses before attackers can at the device level, assembled subsystems and system levels. Similarly, paying more attention to stringent authentication, access controls and network segmentation now becomes imperative considering that 5G networks are much more distributed and complex.
While 5G's arrival will undoubtedly transform industries and economies, its security implications demand close attention and ongoing hardening efforts. Only by proactively identifying and remediating vulnerabilities we all can maximize the benefits of 5G and ensure that crucial infrastructures of tomorrow remain resilient against evolving threats.

Shuttleworth antique cars race & airshow 2023
1 October 2023 Reading time: ~1 minute
Step back in time with us as we take you to the Shuttleworth exhibition of iconic car and air display, where history comes alive amidst the thrill of speed! This truly unique event is a must-see for any enthusiast of vintage motoring and aviation. Witness some of the world's most extraordinary antique cars - sleek pre-war racing machines, elegant Rolls-Royces, and even some of the first ever Fords - take to the track in a display of precision driving that will leave you breathless. Meanwhile, above the ground, an equally impressive array of vintage aircraft, from biplanes to monoplanes, showcase the incredible craftsmanship and innovation of early aviation. Every vehicle on show has been meticulously restored to its former glory, offering a rare glimpse into an era when technology and beauty went hand in hand. Let us take you through this captivating collection of photographs capturing every detail of these magnificent machines in action.
Antique car exhibition and car race
Airplanes display and airshow

Burghley Cross Country
2 September 2023 Reading time: ~1 minute
The annual Burghley Horse Trials, a premier three-day event that has captivated the equestrian world since its inception in 1961. Set amidst the stunning surroundings of Burghley House Estate in Lincolnshire, England, this cross country competition brings together the finest horse and rider combinations from across the globe to face a gruelling yet breathtaking course of natural obstacles set against an unparalleled backdrop of English countryside beauty. The event has a unique atmosphere that cannot be matched anywhere else on earth - where horses are pushed to their limits amidst the unspoiled landscape, creating a spectacle of raw power, skill and elegance. With its challenging terrain and majestic setting, it is little wonder that Burghley continues to captivate both competitors and spectators alike. This blog gallery will take you through the key moments from each year's event, showcasing the artistry and prowess of both horse and rider as they navigate this treacherous yet beautiful course. Join us on a journey through the highs and lows, triumphs and tribulations of Burghley Cross Country - an event that truly has no equal in the equestrian world.
Burghley Cross Country 2024
Burghley Cross Country 2023
Draft 1 of MEF W131 released
28 July 2022 Reading time: 3 minutes
Probably I should have published this news much earlier, but as they say, "better late than never". So here we go: I am delighted to announce that Metro Ethernet Forum (MEF) formally issued Draft Release 1 of MEF Secure SD-WAN Certification Test Requirements (MEF 131). As a nominated editor, I was leading this project for a year, and happy to see that now it has been released.
A quick intro to SD-WAN: it is an acronym for Software-Defined Wide Area Networking. It is a networking paradigm that promises to change the way we think about networking. In a nutshell, SD-WAN technology is a software-defined solution that allows the network to be centrally managed. This leads to a whole new way of designing, deploying and managing the network that is less complex, more flexible, and more user-friendly. The SD-WAN solutions are based on a suite of software and hardware components and can be deployed on various platforms and technologies. SD-WAN delivers a flexible and cost-effective infrastructure to support a unified data centre in the cloud where all applications and servers can reside and interconnect with the network and each other, resulting in lower Total Cost of Ownership and simplified network architectures. At the same time, it is important to know that the last thing you want is when yours or your customers’ data is compromised due to an insecure network, so it is imperative to have a clear understanding of how SD-WAN should be secured before going live.
Now a bit more about the document. MEF 131 describes the certification test requirements needed to verify that a service conforms to MEF 88, which outlines requirements for Application Flow Security for SD-WAN Services. The requirements in MEF 88 have been analyzed to determine which ones are valuable and testable, and this standard outlines the certification test requirements for those requirements. This standard also includes the ACTP Test Plan and ACTP Test Report, which specify the detailed test requirements and test cases, respectively. MEF 88 requirements were mapped to a set of Test Cases:
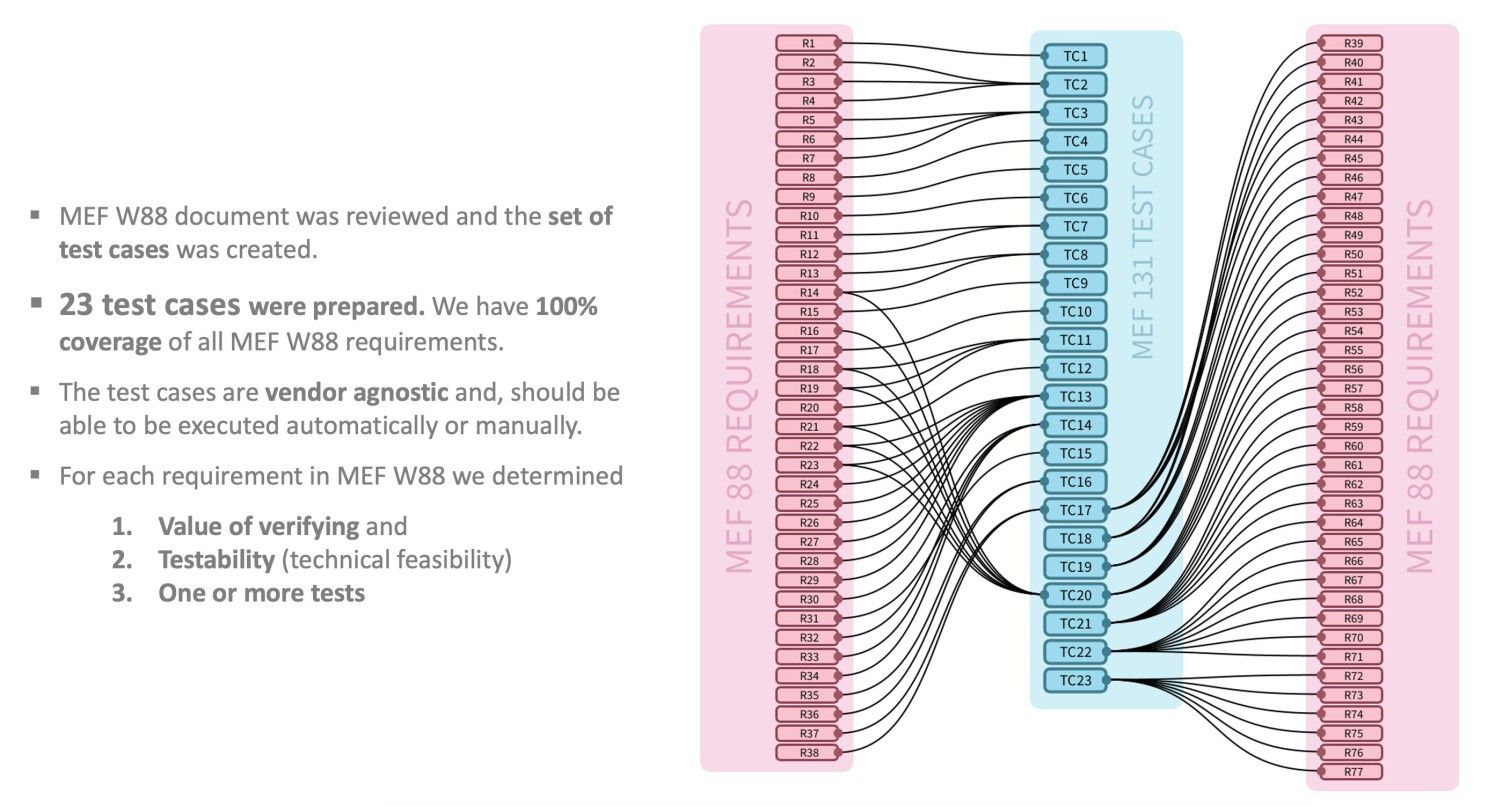
Each Test Case can cover one or more MEF 88 Requirements. This is possible due to the fact that each Test Case can have one or more Tests. There is no mandatory direct relationship between the number of Tests and related Requirements, as one Test can cover more than one MEF 88 Requirement.
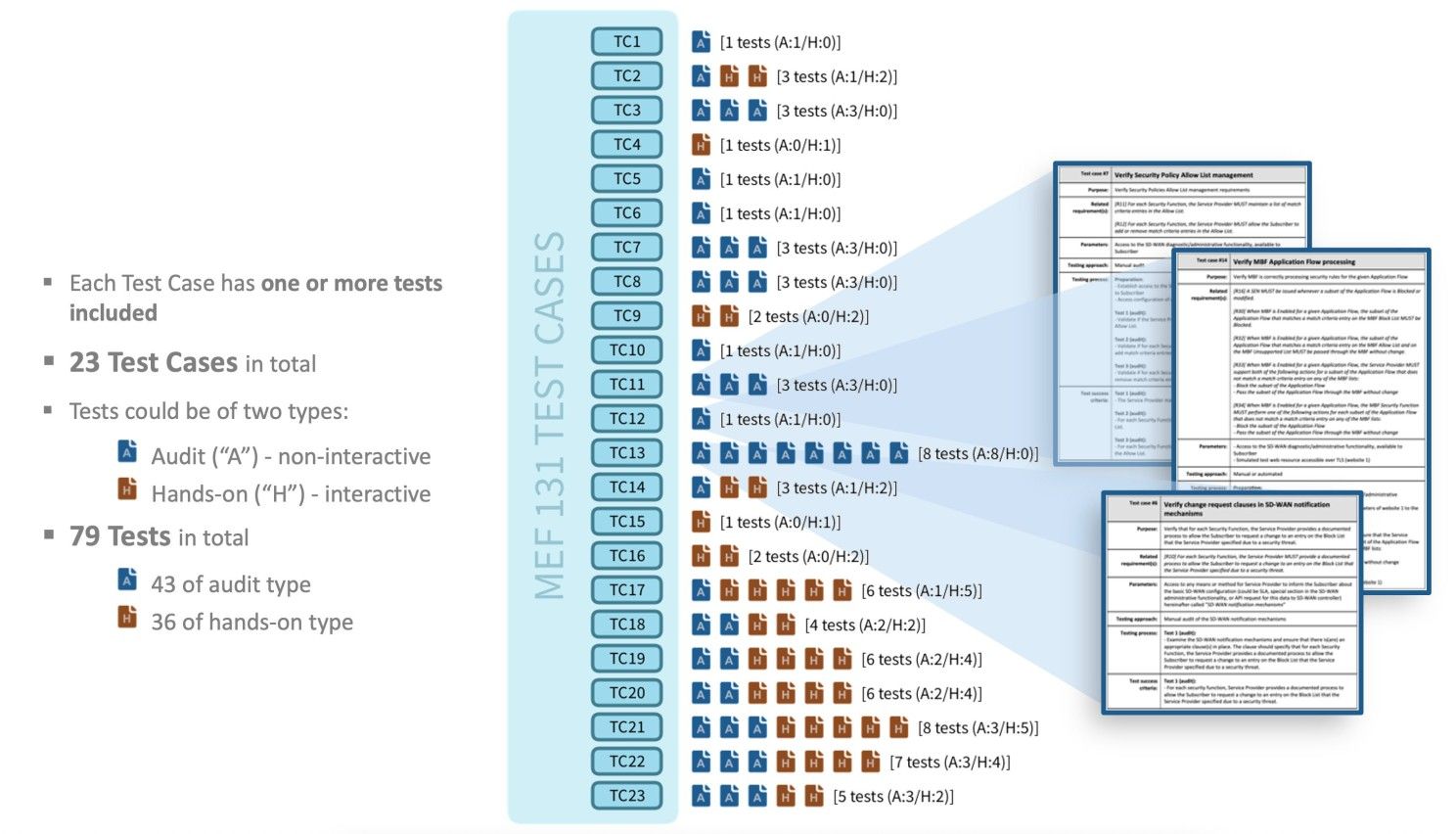
It was a very interesting project, and I am happy to have a chat with you if you want to know more about it and also learn a thing or two about the cybersecurity of SD-WAN.
So the document is publicly available, and I think it is a good time to say thank you for the tremendous support: my colleagues from Spirent Communications and also from MEF members.