Breaking the fear of tomorrow
3 March 2022 Reading time: 3 minutes
You know, I don't write about politics. On the contrary, I stay away from it as far as possible. But maybe this is the time to break the rule, so let me share a few thoughts.
Two days ago, I was attending the Mobile World Congress in beautiful Barcelona. While walking amongst hundreds of much-too-much overexcited geeks, businessmen and demonstrations of all the unimaginable advances of the "technologies of tomorrow," one thought came to me: what all of it is worth if there is no tomorrow? It was such a strange, surreal feeling. Like being on the stage of the beginning of an apocalyptic movie, where everything looks completely fine, but the viewer is already anticipating that actually, the peace is hanging on a very thin thread...
We are a generation of people who do not know war. If we hear about wars, it is only a bunch of pictures on our TV screen. They are so far from us, so it all looks completely harmless. It does not resonate much inside with anything we've ever experienced before. "These are someone else's problems," we think and continue drinking our morning coffee. Well, it seems we all are in a bit different situation now. And if this situation is not resolved - I am afraid there will be no 5G, no augmented reality, no smart and self-driving cars and mobile phones. The whole civilised humanity will rapidly tumble down from the higher levels of Maslow's pyramid to the very bottom, where we will face nothing but endless basic survival.
Whether we like it or not, it seems the faith of the future might be decided on the streets and fields of the country, which (what an irony!) is the largest in Europe, but not everyone in the world could have pointed at on the map. But now everyone can. Because it is so much clear now that Ukrainians are not fighting only for their motherland. It's about all of us. So we can live in peace, continue to develop science, advance technology and, first of all: so nobody on Earth will ever be afraid of tomorrow.
Many say that these days "information is a weapon". And this type of support is also what Ukraine desperately needs. The global tech industry and hundreds of IT activists are already helping and supporting the freedom of information, which is phenomenal. I think this is desperately needed on both sides of the barricade. I also think it is very important that not only the giants of the tech industry but all of us: IT business professionals, not stay aside from the situation. We all should do what we can to support by any means the fight for the freedom of Ukraine. It's not their fight. It's our fight. Fight the future of the whole civilised world: the world of peace, the world as we really want it to be.
Why Amazon is storing my private WiFi passwords?
1 February 2021 Reading time: ~1 minute
The story is short: I am de-registering my Kindle Paperwhite from Amazon and this is what see during the process:
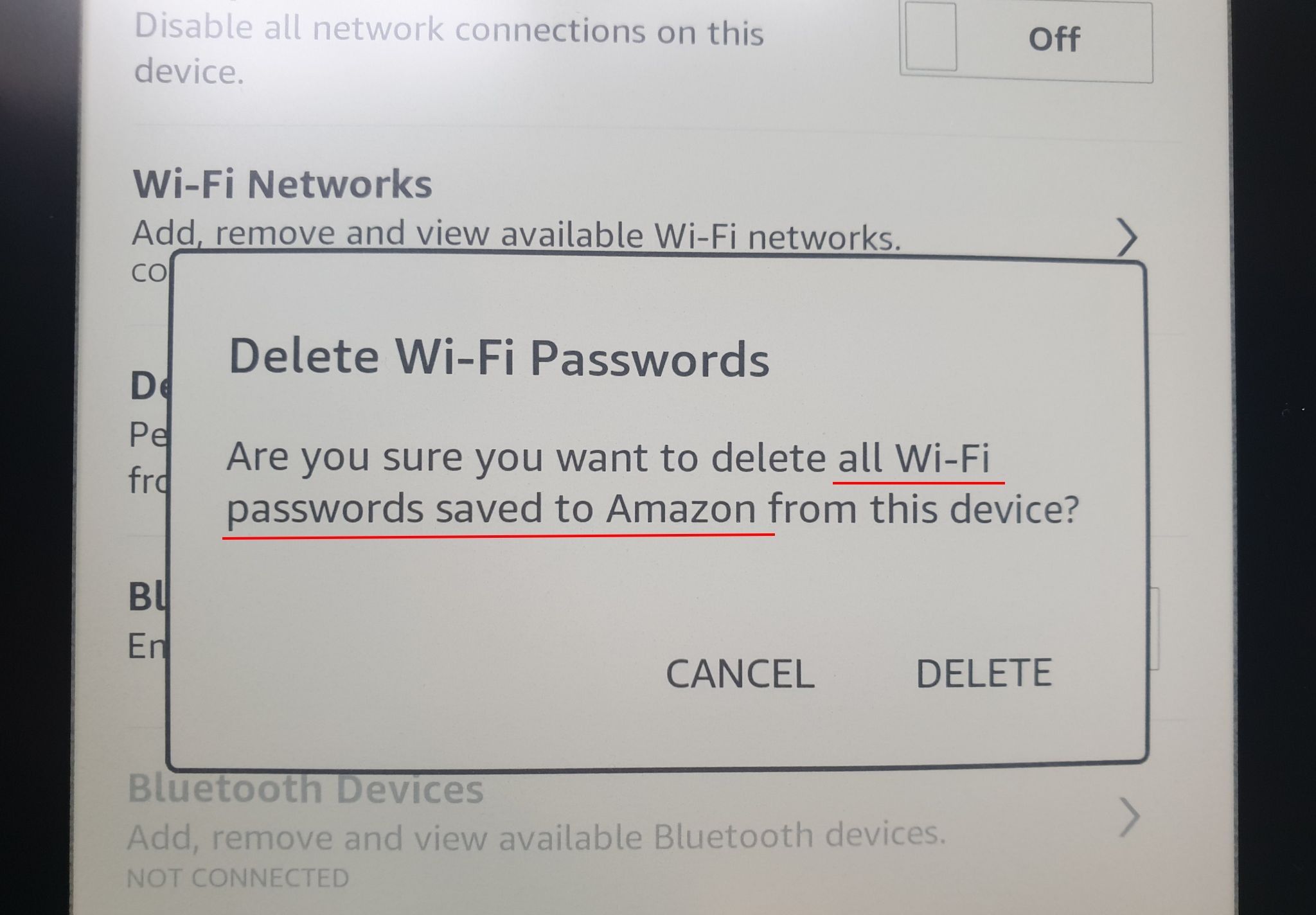
I was genuinely astonished when I saw this question. So is there anybody who can enlighten me: why on earth does Amazon store in the cloud my private WiFi passwords? Ok, I understand that maybe (I said: maybe) there is some genuine reason to keep all the details about what I read, how quickly, how often I turn pages and at what time I switch on or off the backlight. But storing my WiFi passwords in the cloud? How much it does "enhance" my user experience? Should I ask another question: did I allow this? (Oh my bad, probably it is somewhere on page 543 in T&Cs.)
Introduction to IoT security
6 October 2020 Reading time: ~1 minute
An overview of vulnerabilities in hardware devices (in this case: it's a home router) and an illustration of the hacker's/pentester's approach to security analysis and exploitation of embedded/IoT devices.
Hacking car codes - central lock security primer
6 October 2020 Reading time: ~1 minute
This video is about automotive vulnerabilities and an illustration of the attack on the car key system by intercepting and decoding wireless signals.
Insecurity of Industrial Control System (ICS)
5 October 2020 Reading time: ~1 minute
A video about vulnerabilities in industrial systems and a demonstration of hackers exploiting electricity distribution systems (e.g., National Grid) (simulated attack). Note that the demo you can see in this video I implemented in software (100% virtualised). The hardware demonstrator was publicly available at several conferences, such as RSAC and BlackHat Europe.
It should be noted that the demonstrator was implemented in two versions: one entirely in software, and the other (much more interesting to play with) in hardware. Below are a few images of the ICS security demonstrator presented at different venues. People could come and try their skills in hacking the industrial system right on stage!
There is a small article about how some fellow hackers tried to solve the puzzle at BlackHat Europe in London.
Cross-site Scripting vulnerability explained
5 October 2020 Reading time: ~1 minute
Video explaining what Cross Site Scripting (XSS) vulnerability is and how it can be exploited. The video was made when I was working for 7Safe.